Advanced Cryptography for a Post-Quantum World – Protect Your Critical Assets Now
Fortify Your Critical Assets with Quantum Random Entropy and Post Quantum Cryptography.

Cryptography is under constant threat from both pre-quantum vulnerabilities and post-quantum risks. High-performance computing and cloud advancements have surpassed the capabilities of pseudorandom methods, leaving sensitive data and intellectual property exposed. Nfina addresses these challenges with true random entropy and proven technologies to secure communications and data without impacting performance.
Current Enterprise Data Security Challenges
Both industry and government sectors must upgrade their IT systems to achieve quantum resilience
Data Classification and Management
- Organizations struggle to scan and classify data
- Limited resources available
- Lack of organizational cybersecurity policies
- Substandard algorithms pose challenges
Technology Limitations
- Narrow subsets of problems are addressed
- Poor integration of new technologies
- Short track record with new tools
- Accreditation hurdles
Inadequate Risk Remediation
- Risk are identified without offering solutions
- Organizations struggle to remediate risk and policy violations
- Lack of clear paths to compliance
- Disconnect between risk assessment and remediation strategies

Rethinking Cryptography:
The Post-Quantum Threat
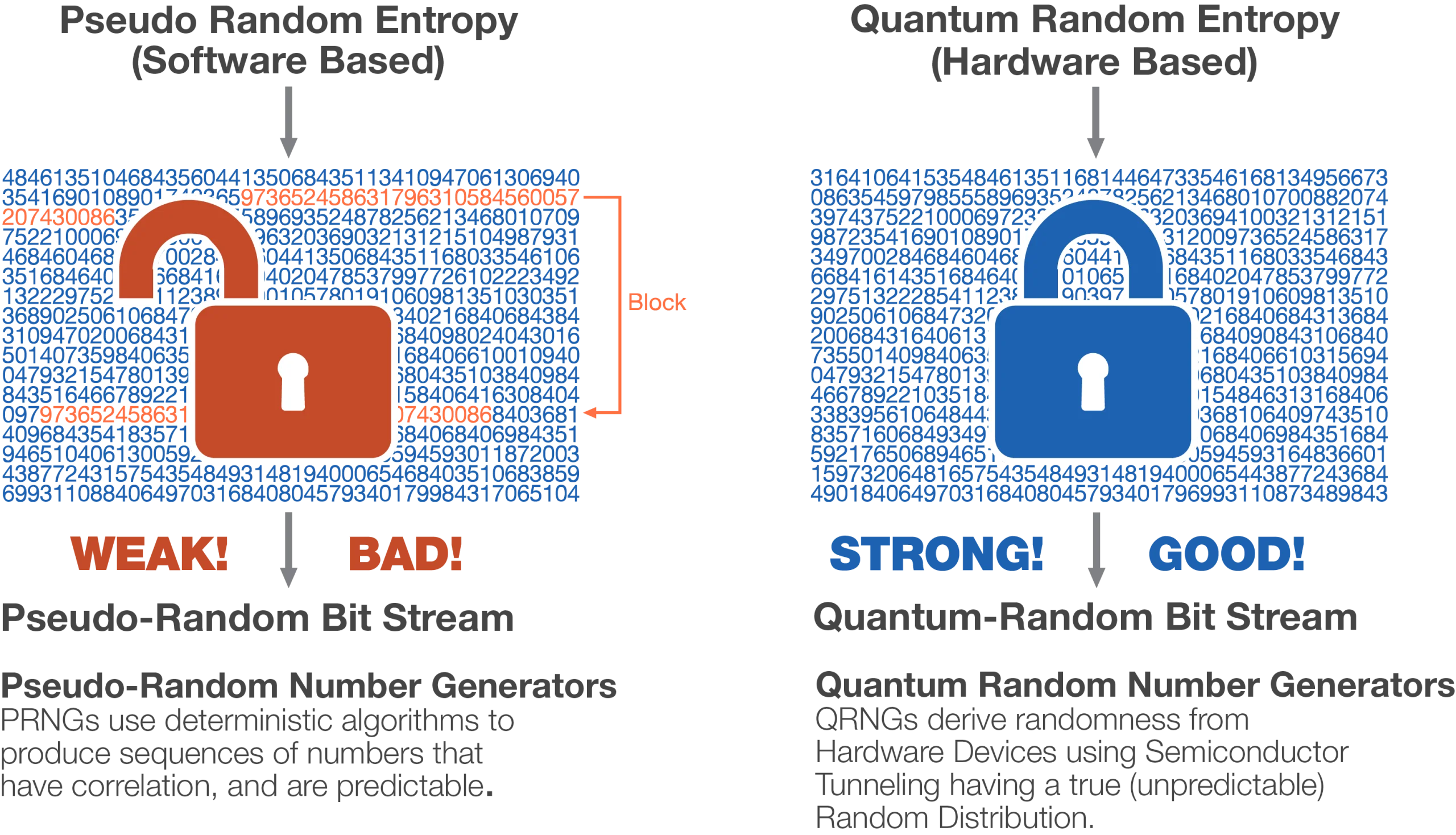
Today’s cryptography relies on pseudo-random number generation (PRNG), the foundation of all cryptographic systems. While PRNG and pseudo-random methods have been trusted for decades, modern supercomputers and cloud technologies now exploit its vulnerabilities, making cryptography as ineffective as a rusty old lock, leaving sensitive data exposed.
Random Number Generation
Securing Financial Services in the
Age of Harvest Now, Decrypt Later
The Post-Quantum Threat
Financial institutions are under increasing threat from sophisticated hacking strategies, such as Harvest Now Decrypt Later (HNDL) which exploit vulnerabilities in current cryptography methods.
- Gartner forecast that traditional cryptography (AES, VPN, etc.) will be vulnerable and obsolete by 2029.
- Large Financial Institutions are already moving to on-prem Hardware Root of Trust.
- Non-Compliance and breaches of cardholder data results in heavy fines.
- Strengthened security deters hackers from targeting your data

Source: EY
Enthropy Security:
What Not to Do
Relying on foreign-owned entropy providers using untrusted components.
Failing to utilize a true hardware root of trust.
Underestimating or not recognizing risks and their potential impacts.
Wasting time and resources conducting studies instead of acting immediately.
Choosing ineffective tools that fail to address cryptographic challenges.
Avoiding Critical Post Quantum Cryptography Errors
Misjudging the urgency of post quantum cryptography risks can leave organizations exposed to critical vulnerabilities. These include:
Assuming “Quantum is far off” and delaying action.
Believing “We aren’t a target” while data is being harvested now.
Creating crypto inventories that expose vulnerabilities.
Ignoring NIST guidance, risking compliance failures.
Standards Driven
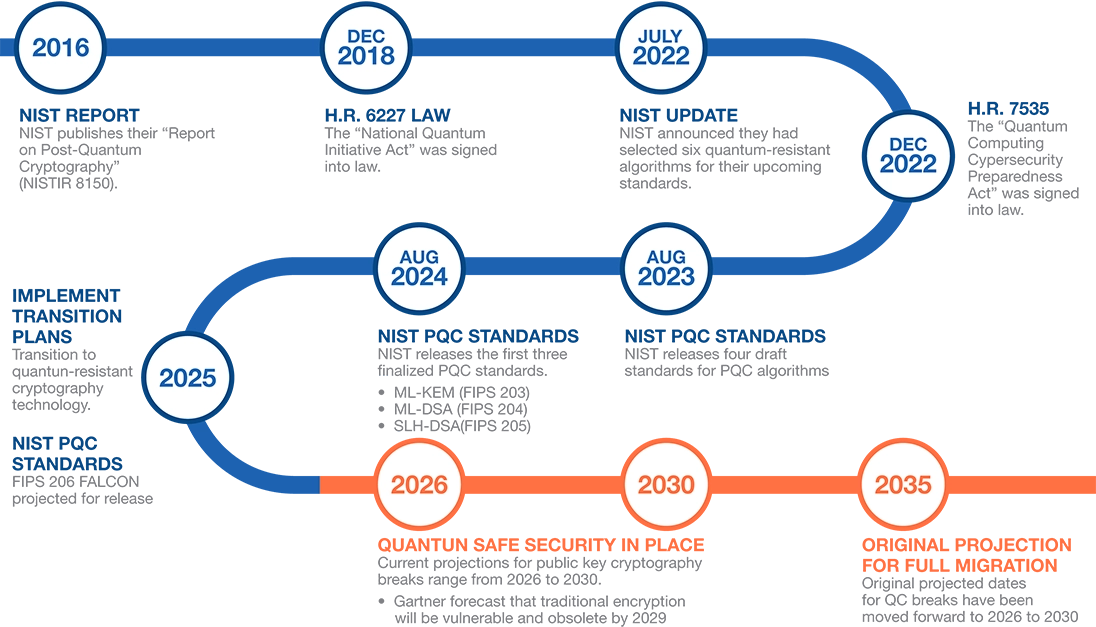
Recently published NIST standards “start the clock” on Federal plans for compliance and remediation and thus creates immediate need for customers to enhance cryptography.
- Hardware Based True Random Entropy Complies with:
- DFARS 252.204-7012, PCI-DSS, FIPS 140-3, NIST SP 800-171/172, FedRAMP Compliant
- True Random “Seed”: quantum random numbers with full entropy at 1Gbit/sec
- Entropy-as-a-Service: push-button deployment meets NIST 800-5
- EntropiQ is CMMC Compliance Standard: basis for SOC II, HIPPAA, ISO27001
PQC Reaches an Inflection Point
Nfina Guidance for Securing Your Post-Quantum Future
Implementing effective post quantum cryptography requires a solution that ensures security, flexibility, and compliance. Nfina provides clear guidance to avoid vulnerabilities and maximize protection.
- Choose a solution that supports on-prem, hybrid, and cloud environments.
- Insist on a hardware root of trust for safety and tamper resistance with frictionless deployment.
- Utilize securely hosted HSMs, separate from cloud services, to prevent warrantless searches.
- Utilize true random entropy for Standards compliance to strengthen post quantum posture.
- Utilize fault tolerant cluster technology for redundancy, not a single entropy source.
Enhance Existing Infrastructure with
Post-Quantum Security

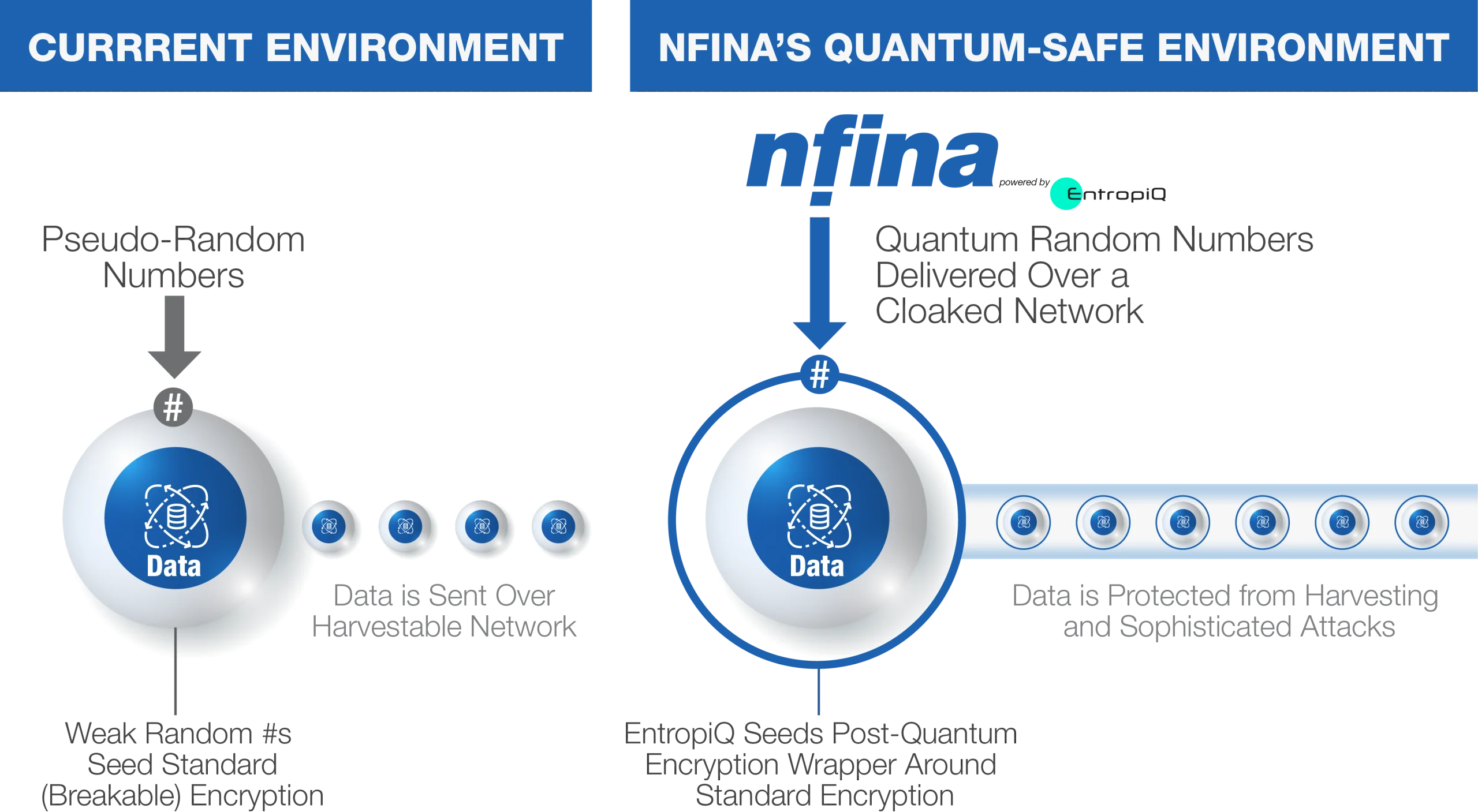
Transforming Cryptography: From Vulnerability to Quantum Safety
In the current environment, cryptography relies on weak pseudo-random seeds, leaving data vulnerable to harvesting and decryption by sophisticated attackers. Nfina’s quantum-safe environment uses quantum random numbers delivered over a cloaked network, wrapping standard cryptography with post-quantum security to protect data from threats.
Data Security Challenges
Data Classification and Management
- Organizations struggle to scan and classify structured and unstructured data
- Limited resources available for risk interpretation and mitigation
- Lack of organizational cybersecurity policies, practice, and enforcement
- Substandard algorithms pose challenges for repair and optimization
Technology Limitations
- Emerging solutions address only narrow subsets of problems
- Poor integration of new technologies with existing systems
- Short track record of new tools increase adoption risks
- Accreditation hurdles for novel technologies
Inadequate Risk Remediation
- Current approaches often only identify risks without offering solutions
- Organizations struggle to triage and remediate risk and policy violations
- Lack of clear, actionable paths to compliance
- Disconnect between risk assessment and practical remediation strategies
Nfina Approach
Precision Risk Targeting
Rapidly identify and remediate vulnerable areas
Crypto Service Enhancement
Strengthen existing cryptographic infrastructure
Entropy Optimization
Boost enterprise-wide randomness quality
Hardware-Based Security
Leverage trusted hardware foundations
Flexible Deployment
Available via Equinix for on-premises, hybrid, and cloud environments
Secure Data Handling
Results stored in protected, customer-owned database
Data Sovereignty
Full customer control; no vendor or provider access
Scalable Architecture
Extensible design to address evolving system needs
Zero Trust
Foundational support for zero trust networks
Progress Tracking
Comprehensive reporting for management and auditors
Nfina Key Differentiators
Quantum-Ready Platform
Gain immediate advantage in the quantum algorithm race
Easy Deployment
No quantum or crypto expertise required
Seamless Integration
Non-disruptive implementation with minimal operational impact
Cost-Effective
Bypass expensive, time-consuming market surveys and product comparisons
Best-in-Class Security
Combines top technologies with intelligence community-grade protection
Proven Performance
Immediate Action
Avoid endless study phases; start improving security now
Adaptive Framework
Continuously evolves to address emerging quantum threats
Nfina Immediate Results
Comprehensive Risk Management
Rapidly identify and mitigate vulnerabilities across all systems
Enhanced Cryptographic Resilience
Strengthen existing crypto services against emerging threats
Accelerated Compliance
Achieve positive audit results and management reporting in weeks, not months
Improved Randomness Quality
Measurable Progress
Rapid ROI
Future-Proof Security
Our Entropy Packages
Small Business
$500
per month
Up To 5MB / mo
$100 per MB
78,125 Keys*
Midsize
$2,500
per month
Up To 40MB / mo
$62.50 per MB
625,000 Keys*
Enterprise
$10,000
per month
Up To 200MB / mo
$50 per MB
3,125,000 Keys*
Large Enterprise
/ Government
$17,500
per month
Up To 500MB / mo
$35 per MB
7,812,000 Keys*
* At 512-bits
